FIN11 Hackers Spotted Using New Techniques In Ransomware Attacks Targeting Financial Institutions and Banks.

A financially-motivated threat actor known for its malware distribution campaigns has evolved its tactics to focus on ransomware and extortion.
According to FireEye's Mandiant threat intelligence team, the collective — known as FIN11 — has engaged in a pattern of cybercrime campaigns at least since 2016 that involves monetizing their access to organizations' networks, in addition to deploying point-of-sale (POS) malware targeting financial, retail, restaurant, and pharmaceutical sectors.
"Recent FIN11 intrusions have most commonly led to data theft, extortion and the disruption of victim networks via the distribution of CLOP ransomware" Mandiant said.
Although FIN11's activities in the past have been tied to malware such as FlawedAmmy, FRIENDSPEAK, and MIXLABEL, Mandiant notes significant overlap in TTPs with another threat group that cybersecurity researchers call TA505 , which is behind the infamous Dridex banking Trojan and Locky ransomware that's delivered through malspam campaigns via the Necurs botnet.
It's worth pointing that Microsoft orchestrated the takedown of the Necurs botnet earlier this March in an attempt to prevent the operators from registering new domains to execute further attacks in the future.
High-Volume Malspam Campaigns
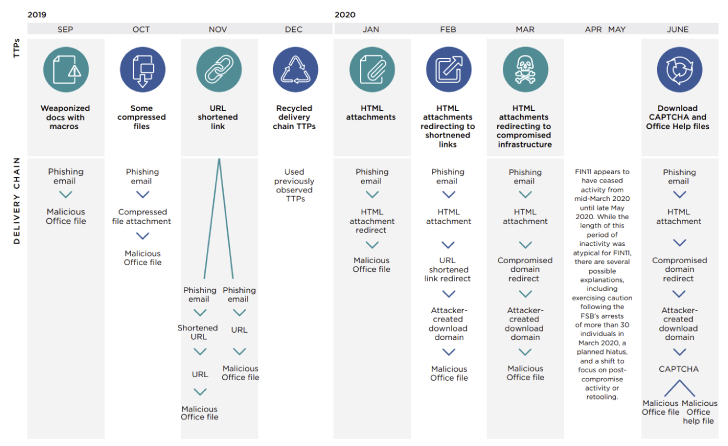
FIN11, in addition to leveraging a high-volume malicious email distribution mechanism, has expanded its targeting to native language lures coupled with manipulated email sender information, such as spoofed email display names and email sender addresses, to make the messages appear more legitimate, with a strong bent towards attacking German organizations in their 2020 campaigns.
For instance, the adversary triggered an email campaign with email subjects such as "research report N-[five-digit number]" and "laboratory accident" in January 2020, followed by a second wave in March using phishing emails with the subject line "[pharmaceutical company name] 2020 YTD billing spreadsheet."
"FIN11's high-volume email distribution campaigns have continually evolved throughout the group's history," Andy Moore, senior technical analyst at Mandiant Threat Intelligence, told The Hacker News via email.
"Although we have not independently verified the connection, there is substantial public reporting to suggest that until sometime in 2018, FIN11 relied heavily on the Necurs botnet for malware distribution. Notably, observed downtime of the Necurs botnet has directly corresponded to lulls in the activity we attribute to FIN11."
Indeed, as per Mandiant's research, FIN11's operations appear to have ceased entirely from mid-March 2020 through late May 2020, before picking up again in June via phishing emails containing malicious HTML attachments to deliver malicious Microsoft Office files.
The Office files, in turn, made use of macros to fetch the MINEDOOR dropper and the FRIENDSPEAK downloader, which then dispatched the MIXLABEL backdoor on the infected device.
A Shift to Hybrid Extortion
In recent months, however, FIN11's monetization efforts have resulted in a number of organizations infected by CLOP ransomware, in addition to resorting to hybrid extortion attacks — combining ransomware with data theft — in a bid to force businesses into acquiescing to extortion payments that range from a few hundred thousand dollars up to 10 million dollars.
"FIN11's monetization of intrusions via ransomware and extortion follows a broader trend among financially motivated actors," Moore said.
"Monetization strategies that have been more common historically, such as the deployment of point-of-sale malware, limit criminals to targeting victims in certain industries, whereas ransomware distribution can allow actors to profit from an intrusion into the network of nearly any organization.
That flexibility, in combination with increasingly frequent reports of ballooning ransom payments, makes it an extremely attractive scheme for financially motivated actors," he added.
What's more, FIN11 is purported to have made use of a wide variety of tools (e.g., FORKBEARD, SPOONBEARD, and MINEDOOR) purchased from underground forums, thereby making attribution difficult or accidentally conflating activities of two disparate groups based on similar TTPs or indicators of compromise.
An Actor of Likely CIS Origin
As for the roots of FIN11, Mandiant stated with "moderate confidence" that the group operates out of the Commonwealth of Independent States (CIS) owing to the presence of Russian-language file metadata, avoidance of CLOP deployments in CIS countries, and the dramatic fall in activity coinciding the Russian New Year and Orthodox Christmas holiday period between January 1-8.
"Barring some sort of disruption to their operations, it is highly likely that FIN11 will continue to attack organizations with an aim to deploy ransomware and steal data to be used for extortion," Moore said.
"As the group has regularly updated their TTPs to evade detections and increase the effectiveness of their campaigns, it is also likely that these incremental changes will continue. Despite these changes, however, recent FIN11 campaigns have consistently relied on the use of macros embedded in malicious Office documents to deliver their payloads."
"Along with other security best practices, organizations can minimize the risk of being compromised by FIN11 by training users to identify phishing emails, disabling Office macros, and implementing detections for the FRIENDSPEAK downloader."
Click here to stay tuned on the page for more News and Updates.
THN
#osutayusuf
Comments
Post a Comment