Cybersecurity researchers have shed light on a new dropper-as-a-service (DaaS) for Android called SecuriDropper that bypasses new security restrictions imposed by Google and delivers the malware.
Dropper malware on Android is designed to function as a conduit to install a payload on a compromised device, making it a lucrative business model for threat actors, who can advertise the capabilities to other criminal groups.
What's more, doing so also allows adversaries to separate the development and execution of an attack from the installation of the malware.
"Droppers and the actors behind them are in a constant state of evolution as they strive to outwit evolving security measures," Dutch cybersecurity firm ThreatFabric said in a report shared with The Hacker News.
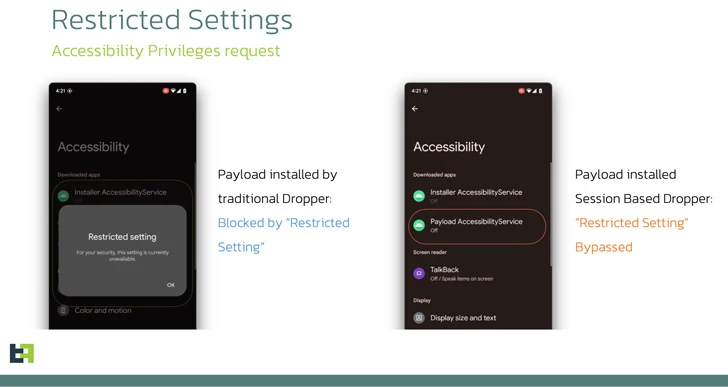
One such security measure introduced by Google with Android 13 is what's called the Restricted Settings, which prevents sideloaded applications from obtaining Accessibility and Notification Listener permissions, which are often abused by banking trojans.
SecuriDropper aims to get around this guardrail without getting detected, with the dropper often disguised as a seemingly harmless app. Some of the samples observed in the wild are as follows -
- com.appd.instll.load (Google)
- com.appd.instll.load (Google Chrome)
"What makes SecuriDropper stand out is the technical implementation of its installation procedure," ThreatFabric explained.
"Unlike its predecessors, this family uses a different Android API to install the new payload, mimicking the process used by marketplaces to install new applications."
Specifically, this entails requesting for permissions to read and write data to external storage.
In the second stage, the installation of the malicious payload is facilitated by urging the victims to click on a "Reinstall" button on the app to resolve a purported installation error.
ThreatFabric said it has observed Android banking trojans such as SpyNote and ERMAC distributed via SecuriDropper on deceptive websites and third-party platforms like Discord.
Another dropper service that has also been spotted offering a similar Restricted Settings bypass is Zombinder, an APK binding tool that was suspected to be shut down earlier this year. It's currently not clear if there is any connection between the two tools.
"As Android continues to raise the bar with each iteration, cybercriminals, too, adapt and innovate," the company said. "Dropper-as-a-Service (DaaS) platforms have emerged as potent tools, allowing malicious actors to infiltrate devices to distribute spyware and banking trojans."
Update#
When reached for comment on the latest findings, a Google spokesperson shared the below statement with The Hacker News -
Restricted settings add an extra layer of protection on top of the user confirmation that is required for apps to access Android settings/permissions. As a core protection, Android users are always in control of which permissions they grant to an app. Users are also protected by Google Play Protect, which can warn users or block apps known to exhibit malicious behavior on Android devices with Google Play Services. We are constantly reviewing attack methods and improving Android's defenses against malware to help keep users safe.
- Get link
- X
- Other Apps
- Get link
- X
- Other Apps

Comments
Post a Comment